Technology with infinite
solutions
Technology with infinite
solutions


We Have Completed
Interconnected systems that enable you to concentrate on your business needs.
Network Security
IT Maintenance
We stay up-to-date with the latest technology trends and offer innovative solutions that help you stay ahead of the competition.
Website Development
We specialize in serving specific industries, such as healthcare, finance, or manufacturing, and offer tailored solutions that meet your unique needs.
Data Management
Our solutions are scalable and can grow with your business, ensuring that you get the most value out of your investment.
Solutions
Providing technology consulting and IT services

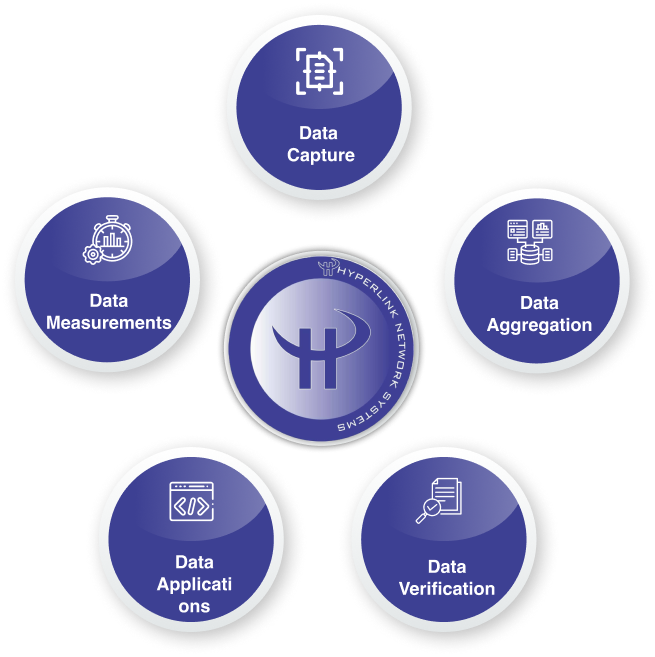
We create fully integrated business systems to help you focus on your core competencies
MAINTAINANCE
Technical Support – Service Level Agreement
Case Priority Level Descriptions
IPR and Source Code
Commercials
Partner with Us for Comprehensive IT
We’re happy to answer any questions you may have and help you determine which of our services best fit your needs.
Your benefits:
- Client-oriented
- Independent
- Competent
- Results-driven
- Problem-solving
- Transparent
What happens next?
We Schedule a call at your convenience
We do a discovery and consulting meeting
We prepare a proposal
Schedule a Free Consultation
Our Client
Cost is always analyzed and negotiated with client’s budget. Any change(s) to the project scope, might result in the revision of the effort estimate and milestone plan provided.















Our Client



















